Critical Remote Code Execution Vulnerability Discovered in CUPS: What You Need to Know
Summary :
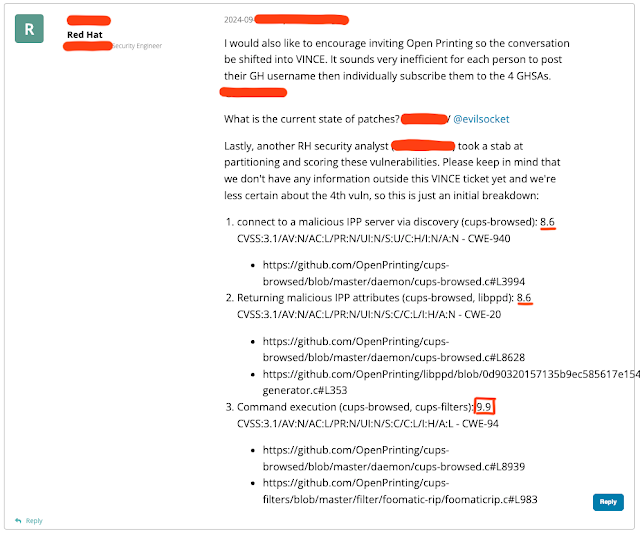
A significant security threat has emerged in the Common Unix Printing System (CUPS) that could affect Linux and other UNIX-based operating systems, including macOS. This vulnerability, identified by Italian security researcher Simone Margaritelli, allows malicious attackers to execute arbitrary commands on vulnerable systems. The flaw comprises four distinct CVEs (Common Vulnerabilities and Exposures): CVE-2024–47176, CVE-2024–47076, CVE-2024–47175, and CVE-2024–47177.
Overview of the Vulnerabilities:
1) CVE-2024–47176:
This issue involves the cups-browsed service, which listens on UDP port 631.It trusts incoming packets from any source, allowing attackers to trigger the Get-Printer-Attributes IPP request to a malicious server URL.
2) CVE-2024–47076:
The libcupsfilters library fails to validate IPP attributes returned from an IPP server. This oversight allows an attacker to feed controlled data to the rest of the CUPS system.
3) CVE-2024–47175:
In this case, the libppd library does not validate IPP attributes when writing them to a temporary PPD file. This can lead to the injection of malicious data into the resulting PPD file.
4) CVE-2024–47177:
The cups-filters component permits arbitrary command execution through the FoomaticRIPCommandLine PPD parameter, further widening the attack surface.
Keynotes:
Margaritelli demonstrated these vulnerabilities on an updated Linux system running cups-browsed version 2.0.1, specifically using Ubuntu 24.05.1 LTS.
The flaws are not limited to Linux, as they affect various UNIX-based systems, although default installations of Red Hat Enterprise Linux (RHEL) are not typically vulnerable.
Exploitation Method:
Attackers can exploit these vulnerabilities through both WAN and LAN connections. By sending UDP packets to port 631, they can replace existing printer IPP URLs with their malicious counterparts, leading to arbitrary command execution when print jobs are initiated.
A troubling report from Shodan indicates that at least 75,000 CUPS servers are currently exposed and accepting custom packets from untrusted sources.
CVSS Score and Mitigation:
The initial CVSS (Common Vulnerability Scoring System) score for this vulnerability is a concerning 9.9. However, some researchers believe the actual impact may be lower than this score suggests. As of now, there is no official patch available, but there are steps you can take to mitigate the risk.
Recommended Actions:
Disable and Uninstall the cups-browsed Service.If you do not need this service, it’s best to remove it entirely.
Update Your CUPS Package: Ensure your system is running the latest security updates.
Block Port 631: Prevent incoming UDP packets on port 631 from untrusted sources.
Consider Blocking DNS-SD: This additional measure can help mitigate risks associated with service discovery protocols.
Remove CUPS Services and Libraries: If feasible, consider removing all CUPS services, binaries, and libraries from your systems. Avoid using zeroconf, Avahi, or Bonjour listeners if they are not essential.
Conclusion:
With the potential for serious remote code execution, it’s crucial for users and administrators to remain vigilant. Regularly updating your systems and reviewing your configurations can go a long way in protecting against these types of vulnerabilities. Stay informed and take proactive steps to secure your environment against this significant threat.
Thanks for reading till the end haha! Check out my other socials here.
